for Professional photographer Marco Verch
A startup that operates surveillance cameras installed in large companies such as Cloudflare and Tesla and public institutions such as hospitals, police and schools.VerkadaIt was hacked, and an incident occurred in which the images of all the surveillance cameras operated by the company were leaked. The Cloudflare victim herself explains the circumstances and the damage situation of this incident.
About the Verkada camera hack on March 8-9, 2021
https://blog.cloudflare.com/about-the-march-8-9-2021-verkada-camera-hack/
On March 8, 2020, an incident occurred in which the startup Verkada, which manages cloud management services for surveillance cameras, was hacked and images from surveillance cameras such as Coudflare, Tesla, hospitals, prisons and schools were leaked. One of the criminal groups claimed to have access to all recorded data, as well as real-time images from all surveillance cameras.
Regarding this incident, Cloudflare published a report on the circumstances and damage situation of the incident on its blog on March 11, 2021.
Although some reports reported that customer data and databases were leaked, hackers were only able to access the “surveillance camera-related” part, and Cloudflare customer data and databases were not affected at all. . Cloudflare is clear. Also, as for the report that “Cloudflare uses the facial recognition feature of the surveillance camera made by Verkada”, “I don’t use it at all.”
Cloudflare requires confirmation of trustworthiness when authenticating and authorizing each access with respect to its own security.Zero trustHe stressed that the internal system was protected by. Cloudflare also provides customers with services that employ Zero Trust, making it a form that strongly emphasizes the usefulness of Zero Trust.
Cloudflare also “refuted” the criminal group’s allegations. At the time of writing, the tweet in question could not be confirmed because the account was frozen, but Tillie Kottmann, who belongs to the criminal group, claimed on Twitter that “he accessed the laptop of Matthew Prince, CEO of Cloudflare.” immediately after the incident.
However, according to Cloudflare, this claim is considered a lie. First, because CEO Prince has not been to the San Francisco office as part of his response to the new coronavirus infection, this attack on the San Francisco office will not give him access to his laptop … The second The reason is that even if a hacker can access the laptop, he protects the data with Zero Trust.Access to CloudflareIt is impossible to break and seize access control rights protected by physical keys.
“I have a root shell on the Cloudflare network,” Kottmann said.
In this regard, Cloudflare says: “It sounds scary, but we do not believe in corporate networks. We use products like Cloudflare Access to control access to resources. Networks are important. Access control is important, not the case,” he said. . , saying that even if you had a root shell on the network, it wouldn’t affect many people as long as you adopted Zerotrust.
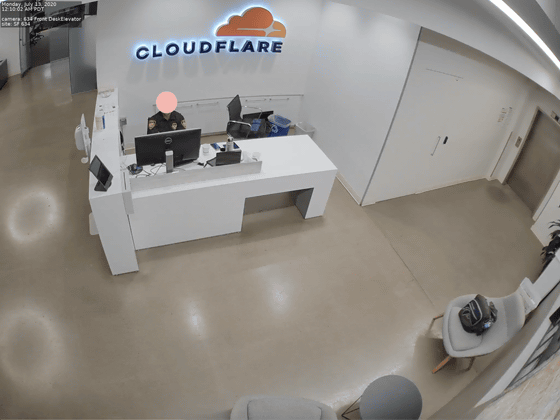
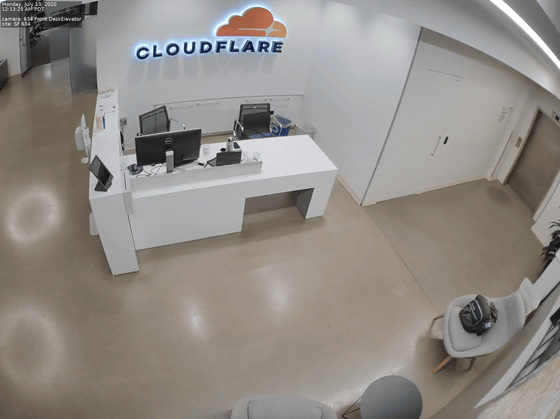
It also explains the video leaked by Cloudflare. According to Cloudflare, the hacker downloaded video recordings from two surveillance cameras installed in the lobby of Cloudflare’s San Francisco office in an attack on Verkada. The downloaded video recording was until July 13, 2020 and the still image was as follows.
Tesla, which was cited with Cloudflare as a large company damaged by the Verkada incident, said: “In China, only one factory in Henan province owned by a contracted supplier was damaged in Shanghai. Gigafactory and showroom are irrelevant.” .commentarydoing.
In response to a series of incidents, Bloomberg testified to a former employee that “Verkada was able to access privileged administrator accounts even for sales staff and trainees.”Press.. Raises questions about the company’s security awareness.
Copy the title and URL of this article.

Introvert. Beer guru. Communicator. Travel fanatic. Web advocate. Certified alcohol geek. Tv buff. Subtly charming internet aficionado.